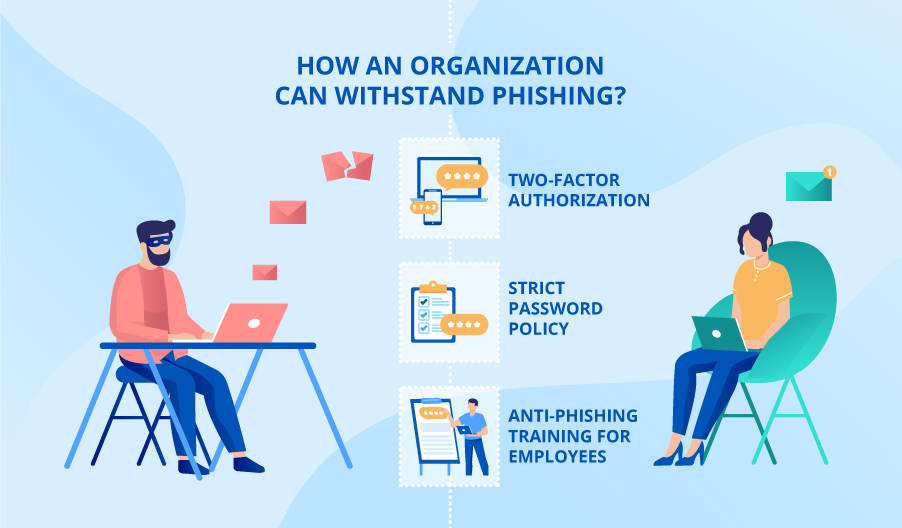
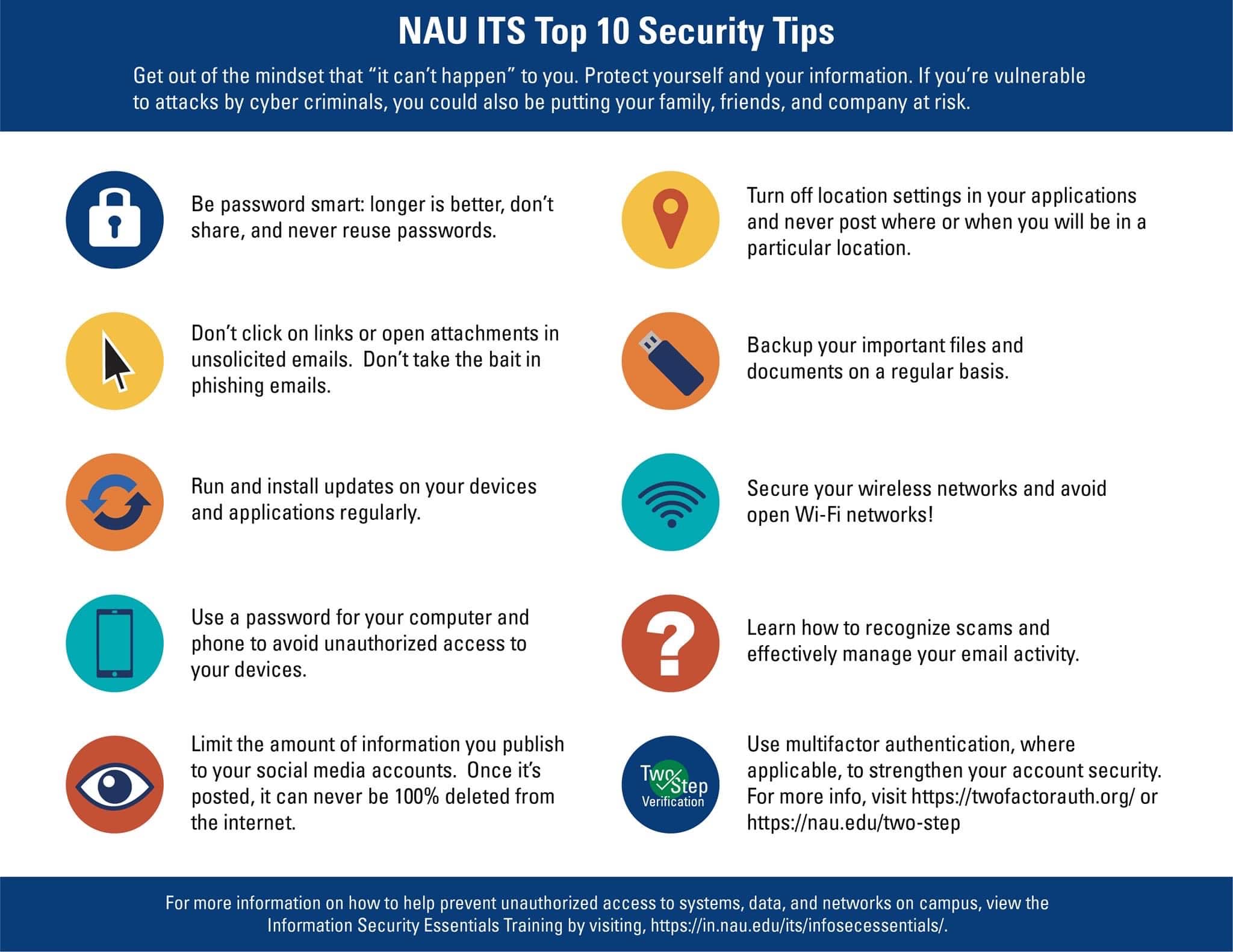
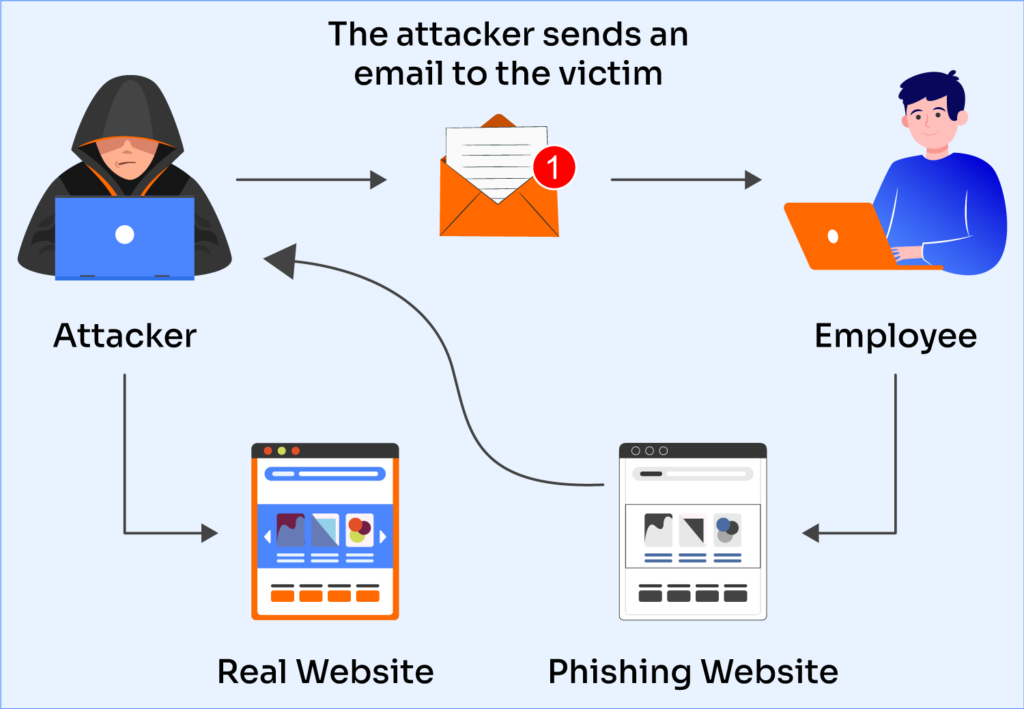
Preventing Phishing Attacks Best Practices - It is no secret that many phishing threats stem from email. 7 best practices to prevent phishing attacks 1. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify.
It is no secret that many phishing threats stem from email. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify. 7 best practices to prevent phishing attacks 1.
It is no secret that many phishing threats stem from email. 7 best practices to prevent phishing attacks 1. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify.
Blog Centex Technologies How To Prevent Phishing Attacks
7 best practices to prevent phishing attacks 1. It is no secret that many phishing threats stem from email. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify.
Don’t Get Hooked How to Recognize and Avoid Phishing Attacks
It is no secret that many phishing threats stem from email. 7 best practices to prevent phishing attacks 1. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify.
Phishing Protection Checklist How To Protect Yourself From Phishing
7 best practices to prevent phishing attacks 1. It is no secret that many phishing threats stem from email. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify.
Password Protection Detecting and Preventing Phishing Attacks RelyPas
7 best practices to prevent phishing attacks 1. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify. It is no secret that many phishing threats stem from email.
How to Prevent Phishing Attacks 10 Ways to Avoid Phishing
7 best practices to prevent phishing attacks 1. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify. It is no secret that many phishing threats stem from email.
How to Prevent Phishing Attacks on Your Company RealLife Examples and
7 best practices to prevent phishing attacks 1. It is no secret that many phishing threats stem from email. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify.
How to Prevent Phishing Attacks
Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify. 7 best practices to prevent phishing attacks 1. It is no secret that many phishing threats stem from email.
Stay vigilant, be diligent How to protect yourself from phishing
Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify. It is no secret that many phishing threats stem from email. 7 best practices to prevent phishing attacks 1.
Phishing CyberHoot Cyber Library
It is no secret that many phishing threats stem from email. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify. 7 best practices to prevent phishing attacks 1.
7 Best Practices To Prevent Phishing Attacks 1.
It is no secret that many phishing threats stem from email. Cybersecurity requires organizations to spot and respond to an array of threats, some of which are easier to identify.