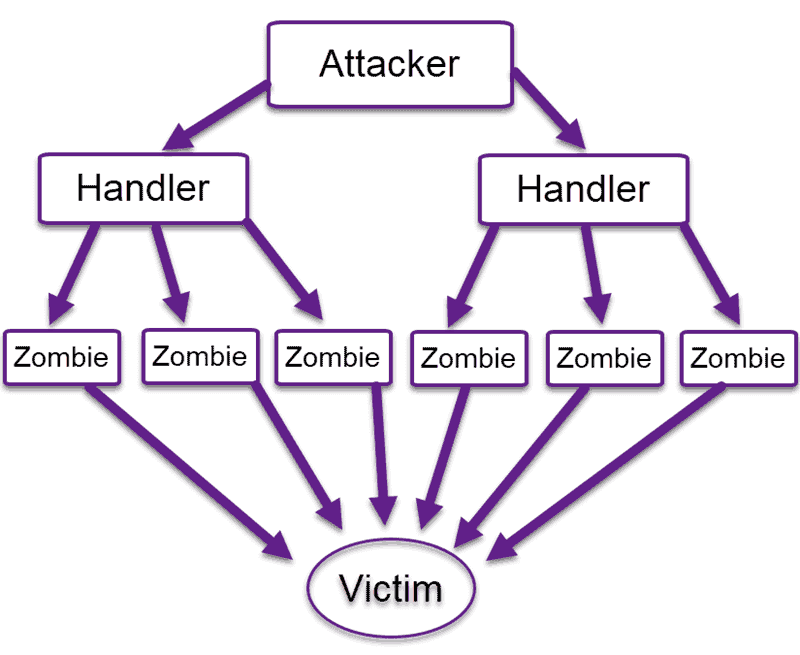
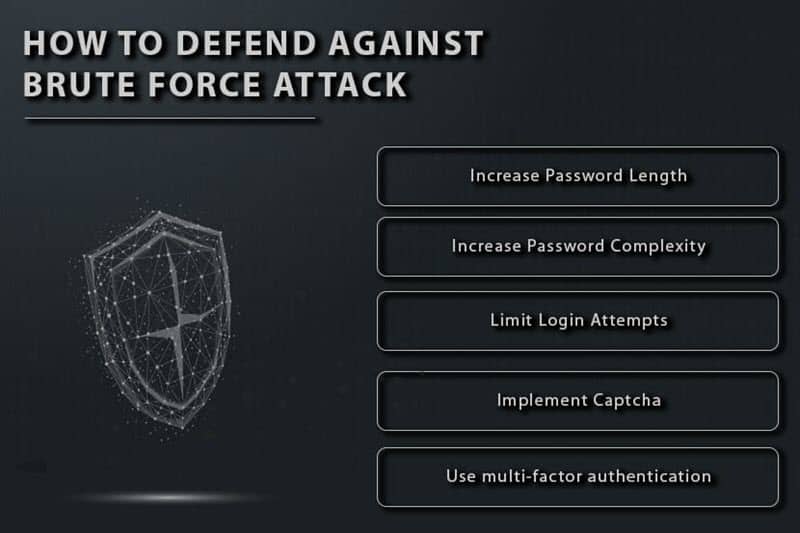
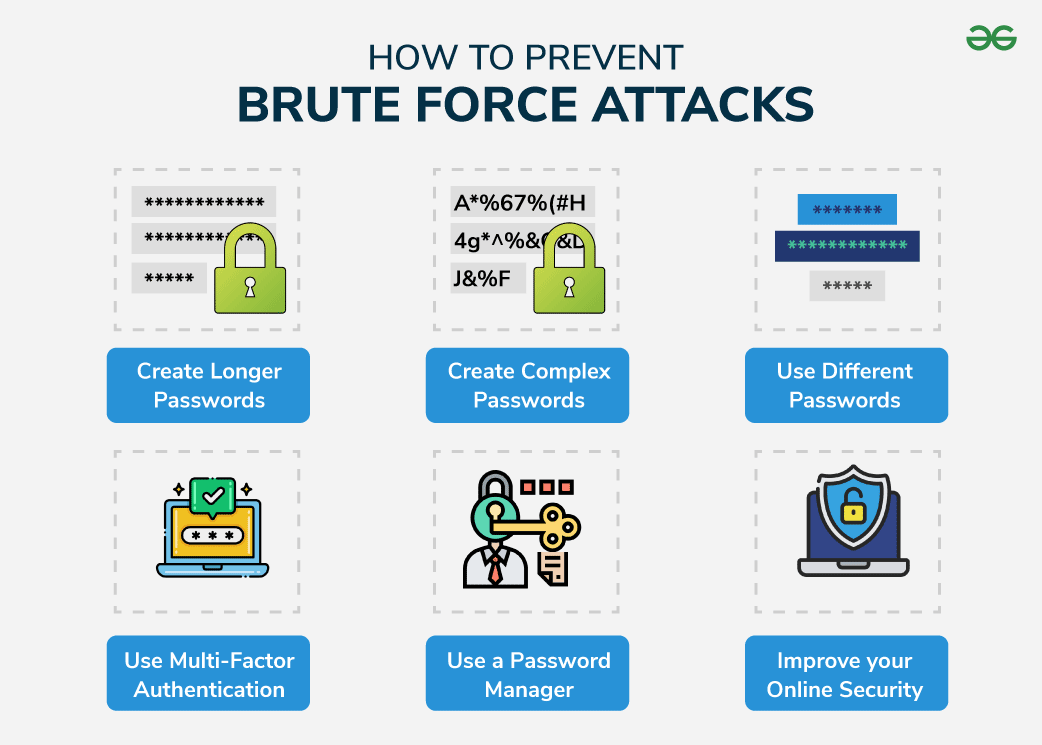
How To Prevent Brute Force Attacks - How to identify brute force attacks. Hackers use trial and error methods to get the user account credentials and steal the information on the. This guide explains 8 methods. If system administrators notice a sudden increase in. Brute force attacks leave obvious clues for server operators. Most server software automatically logs failed login attempts. A brute force attack is an attack where attackers follow a brute force approach to hack usernames and passwords. Brute force attacks are increasingly accounting for the majority of cyberattacks across the world as remote work becomes more prevalent. Prevent brute force attacks by learning how to identify them and implementing the right cybersecurity measures. Read this article to learn more about how to prevent brute force attacks from taking.
Prevent brute force attacks by learning how to identify them and implementing the right cybersecurity measures. A brute force attack is an attack where attackers follow a brute force approach to hack usernames and passwords. Hackers use trial and error methods to get the user account credentials and steal the information on the. Most server software automatically logs failed login attempts. This guide explains 8 methods. Read this article to learn more about how to prevent brute force attacks from taking. If system administrators notice a sudden increase in. How to identify brute force attacks. Brute force attacks are increasingly accounting for the majority of cyberattacks across the world as remote work becomes more prevalent. Brute force attacks leave obvious clues for server operators.
This guide explains 8 methods. Hackers use trial and error methods to get the user account credentials and steal the information on the. Most server software automatically logs failed login attempts. A brute force attack is an attack where attackers follow a brute force approach to hack usernames and passwords. Read this article to learn more about how to prevent brute force attacks from taking. Brute force attacks leave obvious clues for server operators. How to identify brute force attacks. If system administrators notice a sudden increase in. Brute force attacks are increasingly accounting for the majority of cyberattacks across the world as remote work becomes more prevalent. Prevent brute force attacks by learning how to identify them and implementing the right cybersecurity measures.
How to Prevent Brute Force Attacks?
Prevent brute force attacks by learning how to identify them and implementing the right cybersecurity measures. If system administrators notice a sudden increase in. Read this article to learn more about how to prevent brute force attacks from taking. Hackers use trial and error methods to get the user account credentials and steal the information on the. A brute force.
How to Prevent Brute Force Attacks Programming Cube
Hackers use trial and error methods to get the user account credentials and steal the information on the. How to identify brute force attacks. Brute force attacks are increasingly accounting for the majority of cyberattacks across the world as remote work becomes more prevalent. If system administrators notice a sudden increase in. This guide explains 8 methods.
How To Prevent Brute Force Attacks With 8 Easy Tactics PhoenixNAP KB
Brute force attacks leave obvious clues for server operators. Read this article to learn more about how to prevent brute force attacks from taking. Most server software automatically logs failed login attempts. A brute force attack is an attack where attackers follow a brute force approach to hack usernames and passwords. Brute force attacks are increasingly accounting for the majority.
How to prevent brute force attacks
This guide explains 8 methods. Hackers use trial and error methods to get the user account credentials and steal the information on the. Brute force attacks are increasingly accounting for the majority of cyberattacks across the world as remote work becomes more prevalent. A brute force attack is an attack where attackers follow a brute force approach to hack usernames.
How To Prevent Brute Force Attacks With 8 Easy Tactics PhoenixNAP KB
Brute force attacks leave obvious clues for server operators. If system administrators notice a sudden increase in. Brute force attacks are increasingly accounting for the majority of cyberattacks across the world as remote work becomes more prevalent. Read this article to learn more about how to prevent brute force attacks from taking. Hackers use trial and error methods to get.
SSH Hardening to Prevent BruteForce Attacks
A brute force attack is an attack where attackers follow a brute force approach to hack usernames and passwords. How to identify brute force attacks. Most server software automatically logs failed login attempts. Prevent brute force attacks by learning how to identify them and implementing the right cybersecurity measures. Hackers use trial and error methods to get the user account.
How To Prevent Brute Force Attacks?
This guide explains 8 methods. Prevent brute force attacks by learning how to identify them and implementing the right cybersecurity measures. Hackers use trial and error methods to get the user account credentials and steal the information on the. If system administrators notice a sudden increase in. Brute force attacks are increasingly accounting for the majority of cyberattacks across the.
How to Prevent Brute Force Attacks Top Strategies SSL Dragon
Hackers use trial and error methods to get the user account credentials and steal the information on the. This guide explains 8 methods. Brute force attacks are increasingly accounting for the majority of cyberattacks across the world as remote work becomes more prevalent. Most server software automatically logs failed login attempts. A brute force attack is an attack where attackers.
How to Prevent Brute Force Attacks Top Strategies SSL Dragon
Hackers use trial and error methods to get the user account credentials and steal the information on the. A brute force attack is an attack where attackers follow a brute force approach to hack usernames and passwords. This guide explains 8 methods. Brute force attacks are increasingly accounting for the majority of cyberattacks across the world as remote work becomes.
How To Prevent Brute Force Attacks? Wp Safe Zone
Read this article to learn more about how to prevent brute force attacks from taking. If system administrators notice a sudden increase in. This guide explains 8 methods. Most server software automatically logs failed login attempts. Brute force attacks are increasingly accounting for the majority of cyberattacks across the world as remote work becomes more prevalent.
Brute Force Attacks Leave Obvious Clues For Server Operators.
A brute force attack is an attack where attackers follow a brute force approach to hack usernames and passwords. Brute force attacks are increasingly accounting for the majority of cyberattacks across the world as remote work becomes more prevalent. Hackers use trial and error methods to get the user account credentials and steal the information on the. If system administrators notice a sudden increase in.
Prevent Brute Force Attacks By Learning How To Identify Them And Implementing The Right Cybersecurity Measures.
This guide explains 8 methods. How to identify brute force attacks. Most server software automatically logs failed login attempts. Read this article to learn more about how to prevent brute force attacks from taking.