How Prevent Spoofing In Cisco - To prevent spoofing in cisco, it is essential to implement various security measures that can help detect and block spoofing. We want to be able to stop malicious users hijacking sessions of users by stealing the ip and assigning it as static ip on their. In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so. Although there is no easy solution for the ip spoofing problem, you can apply some simple proactive and reactive methods at the nodes,.
Although there is no easy solution for the ip spoofing problem, you can apply some simple proactive and reactive methods at the nodes,. We want to be able to stop malicious users hijacking sessions of users by stealing the ip and assigning it as static ip on their. To prevent spoofing in cisco, it is essential to implement various security measures that can help detect and block spoofing. In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so.
In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so. We want to be able to stop malicious users hijacking sessions of users by stealing the ip and assigning it as static ip on their. Although there is no easy solution for the ip spoofing problem, you can apply some simple proactive and reactive methods at the nodes,. To prevent spoofing in cisco, it is essential to implement various security measures that can help detect and block spoofing.
What is Spoofing? Ways to Prevent It PrivacySavvy
In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so. Although there is no easy solution for the ip spoofing problem, you can apply some simple proactive and reactive methods at the nodes,. To prevent spoofing in cisco, it is essential to implement various security measures that can help.
Spoofing Explained What It Is and How to Prevent It
To prevent spoofing in cisco, it is essential to implement various security measures that can help detect and block spoofing. We want to be able to stop malicious users hijacking sessions of users by stealing the ip and assigning it as static ip on their. In this article, we will discuss the importance of preventing spoofing in cisco networks and.
SEC Consult Group on LinkedIn smtp spoofing cisco gmx microsoft
Although there is no easy solution for the ip spoofing problem, you can apply some simple proactive and reactive methods at the nodes,. In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so. To prevent spoofing in cisco, it is essential to implement various security measures that can help.
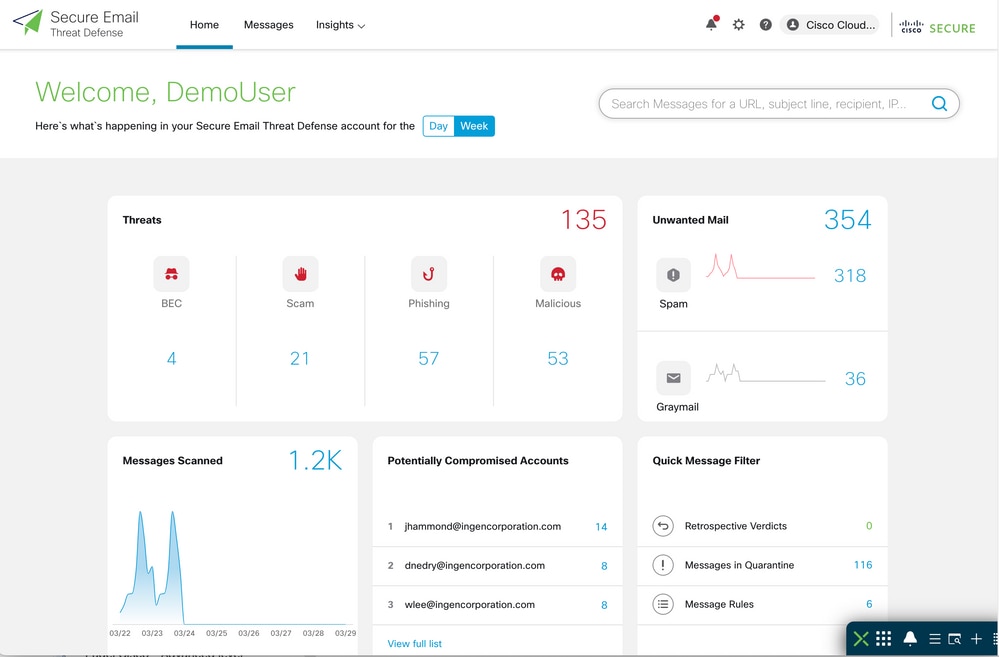
Detect and Prevent Email Spoofing Cisco
To prevent spoofing in cisco, it is essential to implement various security measures that can help detect and block spoofing. In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so. We want to be able to stop malicious users hijacking sessions of users by stealing the ip and assigning.
how to prevent someone from spoofing your phone number Shera Phelan
We want to be able to stop malicious users hijacking sessions of users by stealing the ip and assigning it as static ip on their. In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so. To prevent spoofing in cisco, it is essential to implement various security measures that.
Preventing & Identifying ARP Poisoning or Spoofing Attacks
In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so. Although there is no easy solution for the ip spoofing problem, you can apply some simple proactive and reactive methods at the nodes,. We want to be able to stop malicious users hijacking sessions of users by stealing the.
How to Prevent Spoofing Attacks Pure Cloud Solutions
We want to be able to stop malicious users hijacking sessions of users by stealing the ip and assigning it as static ip on their. In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so. To prevent spoofing in cisco, it is essential to implement various security measures that.
What is IP Spoofing and How to Prevent It? EasyDMARC
In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so. Although there is no easy solution for the ip spoofing problem, you can apply some simple proactive and reactive methods at the nodes,. To prevent spoofing in cisco, it is essential to implement various security measures that can help.
Designing and Deploying Cisco AI Spoofing Detection Part 2 Cisco Blogs
Although there is no easy solution for the ip spoofing problem, you can apply some simple proactive and reactive methods at the nodes,. To prevent spoofing in cisco, it is essential to implement various security measures that can help detect and block spoofing. In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical.
What Is Spoofing? Cisco
In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so. Although there is no easy solution for the ip spoofing problem, you can apply some simple proactive and reactive methods at the nodes,. To prevent spoofing in cisco, it is essential to implement various security measures that can help.
To Prevent Spoofing In Cisco, It Is Essential To Implement Various Security Measures That Can Help Detect And Block Spoofing.
We want to be able to stop malicious users hijacking sessions of users by stealing the ip and assigning it as static ip on their. Although there is no easy solution for the ip spoofing problem, you can apply some simple proactive and reactive methods at the nodes,. In this article, we will discuss the importance of preventing spoofing in cisco networks and provide practical steps to do so.