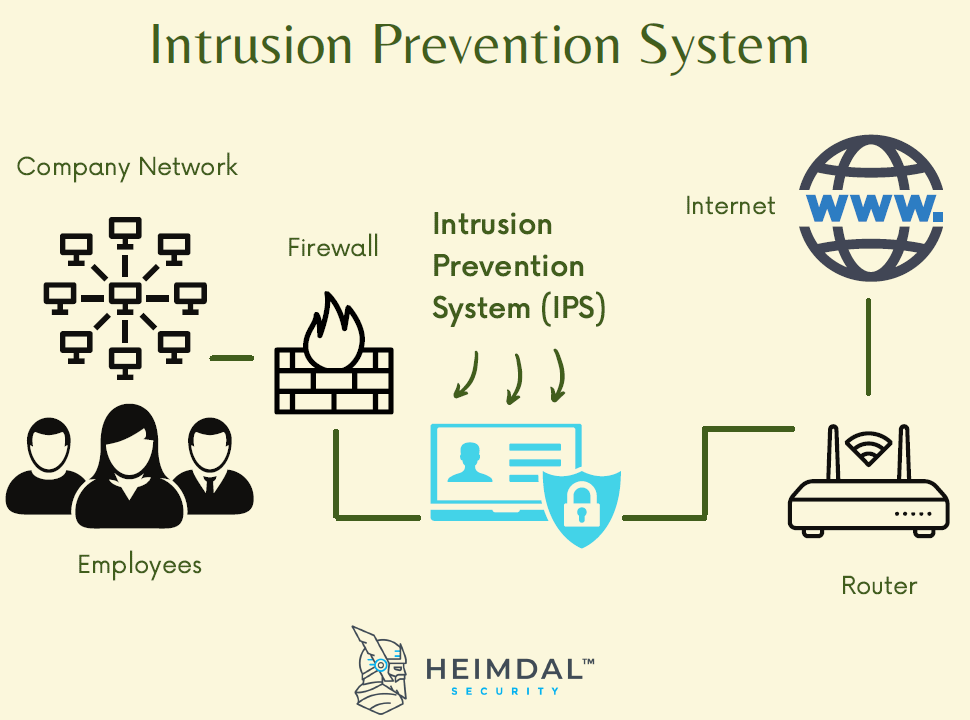
Cisco Intrusion Prevention - Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. This is an opportunity to learn and ask questions about security best practices and. For vulnerability prevention, the cisco. It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces. Configuring cisco ios intrusion prevention system. Stop more threats and address attacks.
Stop more threats and address attacks. It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces. This is an opportunity to learn and ask questions about security best practices and. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. For vulnerability prevention, the cisco. Configuring cisco ios intrusion prevention system.
It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces. For vulnerability prevention, the cisco. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. This is an opportunity to learn and ask questions about security best practices and. Configuring cisco ios intrusion prevention system. Stop more threats and address attacks.
Intrusion prevention system ips lynxlasopa
For vulnerability prevention, the cisco. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces. Configuring cisco ios intrusion prevention system. This is an opportunity to learn and ask questions about security best practices and.
Securing Networks with Cisco Firepower Next Generation Intrusion
Stop more threats and address attacks. Configuring cisco ios intrusion prevention system. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces. This is an opportunity to learn and ask questions about security best practices and.
cisco intrusion prevention system solution
Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. For vulnerability prevention, the cisco. Configuring cisco ios intrusion prevention system. Stop more threats and address attacks. This is an opportunity to learn and ask questions about security best practices and.
Solved Intrusion Events Cisco Community
Configuring cisco ios intrusion prevention system. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces. Stop more threats and address attacks. For vulnerability prevention, the cisco.
(PDF) Cisco IOS Intrusion Prevention System Deployment Guide...Cisco
Configuring cisco ios intrusion prevention system. For vulnerability prevention, the cisco. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces. Stop more threats and address attacks.
Monitor Events Generated by Cisco IOS Intrusion Prevention System using
Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. Configuring cisco ios intrusion prevention system. For vulnerability prevention, the cisco. This is an opportunity to learn and ask questions about security best practices and. Stop more threats and address attacks.
Cisco Intrusion Prevention System Modules for the Cisco Integrated
Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. This is an opportunity to learn and ask questions about security best practices and. Configuring cisco ios intrusion prevention system. It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces. Stop more threats and address attacks.
Intrusion Prevention Fundamentals Cisco Press
Stop more threats and address attacks. For vulnerability prevention, the cisco. This is an opportunity to learn and ask questions about security best practices and. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces.
CISCO IPS 4260 INTRUSION PREVENTION SYSTEM
It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces. This is an opportunity to learn and ask questions about security best practices and. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. For vulnerability prevention, the cisco. Stop more threats and address attacks.
CCNP Security Cisco Secure Firewall and Intrusion Prevention System
For vulnerability prevention, the cisco. This is an opportunity to learn and ask questions about security best practices and. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. Configuring cisco ios intrusion prevention system. Stop more threats and address attacks.
Configuring Cisco Ios Intrusion Prevention System.
Stop more threats and address attacks. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of. It prevents vulnerability by flagging and analyzing suspicious and unidentified files and enforces. For vulnerability prevention, the cisco.